 Web Content Viewer
Web Content Viewer
Resources
Take a "deep dive" into our products and services and learn more about Canon Solutions America's Security capabilities by accessing the resources below.

A Day in the Life of 5 Organizations
Catastrophic data breaches can occur at any time no matter your organization's size or industry. Hackers, unauthorized users, and human error can all affect the strength of your company's security posture. See how different organizations can be affected and how our solutions can help.

Securing Client Data in a Digital Age
Law firm data breaches and related lawsuits are on the rise, highlighting the urgent need for robust client data protection. Despite nearly three-quarters of law firms believing they are more secure than their peers, significant security gaps persist across firms of all sizes. To mitigate these risks, firms should implement strong security protocols. Find out more here...

Refresh Cybersecurity
Securing the workplace demands a thoughtful approach. Security is a collective responsibility. Initiating an effective cybersecurity program requires committment driven by leadership, guiding organizations in allocating human and technological resources effectively. Stakeholders from C-level executives to end users play crucial roles in fostering a secure environment.

PFCaaS No Longer Forgotten Endpoints - Symphion
Printers are often forgotten in endpoint protection plans, Maintain printer secrutiy settings in multi-vendor printer fleets with Printer Fleet Cyberseurity as a Service.

PFCaaS
Unsecured and unmonitored printers on your network can pose significant vulnerabilities to your organization. Watch this video to see how cost-effective printer and IoT security solutions from Canon Solutions America can help minimize risk within your fleet and provide visibility and control.

Future Proofing Your Campus
Higher education institutions like Worcester Polytechnic Institute (WPI) are at the forefront of innovation. Patty Patria, WPI's VP for Information Technology, emphasizes the shift from traditional perimeter-based security to a more comprehensive approach.
Does Your Security Need a Check-up?
The 2023 Cost of a Data Breach Report by IBM and the 2023 Healthcare Data Breach Report from HIPAA Journal show healthcare organizations are facing greater risk while adapting to a patient-centric model and are looking to robust data protection measures.

4 Ways HC Providers Can Help Mitigate Risk
In healthcare, sensitive data like PHI, PII, and financial records is stored in diverse formats and locations. Information can often be exposed through internet-connected devices used by staff. Safeguarding this data is crucial for maintaining patient privacy and organizational security.

Cybersecurity: 4 Overlooked Areas and How To Secure Them
While organizations typically deploy standard cybersecurity tools like firewalls and anti-malware software, achieving robust security in today's workplace requires a comprehensive defense strategy.

Foundational Elements of Security
The cost of a data breach for U.S. businesses continues to rise, encompassing expenses such as ransom payments, productivity losses, response efforts, remediation costs, and damage to reputation. Learn more about foundational elements of cybersecurity.

Security Solutions and Services for Healthcare
SECURITY SOLUTIONS AND SERVICES FOR HEALTHCARE:
Our mission underscores the proactive approach necessary in healthcare IT and security to mitigate inevitable data breach risks across acute and ambulatory care environments.

Mr. Big Cybersecurity Interactive Video
Defending your organization against the threat of cyberattacks is a big deal in today’s complex work environment. Meet Mr. Big and learn how we can help organizations of all sizes proactively secure their business.

5 Pillars eBook
Our Five Pillars of Security model isTailored for all stakeholders and simplifies complex security challenges.

Big Security Solutions
Thoughtful, effective, security solutions are essential for small and mid-size businesses.We've created a comprehensive approach, addressing five key risk areas with simplified options that can be customized to suit your specific needs.
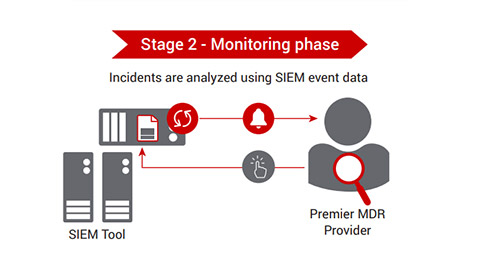
Monitor. Detect. Respond: Three key actions to help avoid a data breach
If your organization experiences a data breach, understanding the entry points, responding promptly is critical. Discover how Managed Detection and Response can safeguard your digital assets.

Securing Multi-Brand Printer Fleets Can Be Easy
Securing large multi-brand printer fleets, which can consist of hundreds or thousands of devices poses challenges. We have cost-effective methods to maintain these security measures across such extensive fleets.

Cybersecurity Starts With Training Your Team
Cybersecurity awareness training is a key component of our Big Security solutions. Keeping your employees are well-informed is crucial—they need to recognize and avoid potential threats.

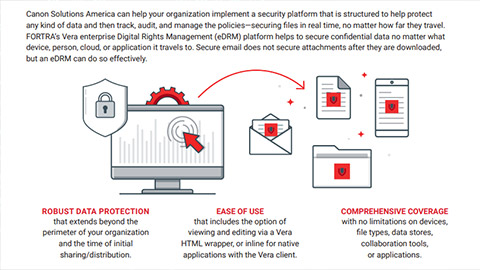
Collaborate Confidently With Integrated Data Security
Achieve secure collaboration by leveraging digital rights management and data classification to ensure comprehensive and seamless protection of your data throughout its lifecycle.
How to Pick a Printer That’s Hard to Hack
Office printers and multifunctional devices, can be vulnerable to cyber attacks similar to computers and servers. It's crucial to enhance your security measures to protect against these potential threats.

Rapid7 T O F Vulnerability Management
Vulnerability management is an essential cybersecurity process that entails identifying, assessing, and remedying security gaps in software, hardware, and networks. Think of it as routine maintenance for an organization's digital infrastructure, ensuring robust protection against cyber threats.

FedRAMP's Role in Supporting Healthcare
Data breaches can harm hospitals and health systems financially, damage their reputation, and hinder their ability to deliver care. Healthcare IT leaders looking to mitigate risks can turn to established frameworks, such as the Federal Risk and Authorization Management Program (FedRAMP), designed to safeguard sensitive information. FedRAMP offers guidelines and tools that could prove beneficial in securing healthcare environments against potential threats.

3 Reasons to Choose a FedRAMP Authorized Print Management Service
Government agencies moving to the cloud benefit from using FedRAMP-authorized services, which adhere to rigorous security standards and simplify compliance with NIST SP 800-53 controls. These services offer streamlined IT management, cost savings through reduced security validation efforts, and enhanced security features like flexible authentication and secure printing capabilities.

5 Pillars of Security Brochure 2024
Security is an ongoing journey through dymanic threat environment that can compromise your information from many different sources. Canon Solutions America's 5 Pillars of Security make the journey easier to navigate.

Cybersecurity Help Wanted
In response to breaches, many organizations surveyed plan to increase security investments. IT decision-makers are considering outsourcing cybersecurity operations to manage costs and gain specialized expertise, citing limitations in in-house IT resources.

Government Agencies Can Help Combat Cybersecurity Threats with a ZERO TRUST Print Security Strategy
Explore some of the security features offered by Canon that can help you create a successful security posture for your government agency. Learn why including your print environment in a Zero Trust strategy helps protect your network and can develop trust from the end user to the device as well as the applications and data that reside on it.
Many variables can impact the security of a customer’s device and data. Canon does not warrant that the use of services, equipment, or related features detailed herein will eliminate the risk of potential malicious attacks, or misuse of devices or data or other security issues.