 Web Content Viewer
Web Content Viewer
Device Security
In this challenging cybersecurity climate, Canon benefits its clients with an on-going commitment to a strong security feature set in our printers and MFP’s. Through our 5 Pillars of Security we can help address risk, improve efficiency and improve incident response in organizations.
Please visit each of our 5 Pillars of Security to see how Canon can help with security in your organization.
Canon’s 5 Pillars of Security presents a portfolio of cybersecurity products and services in a thoughtful way that groups solutions in functional areas. Device Security is key component of our 5 Pillar approach.
Can cybercriminals hijack your office equipment?
Yes. Printers, multifunctional devices, and other networked office equipment can be targets for cybercriminals. If they’re connected to the internet, they can be accessed from outside your office walls. That’s why Canon imageRUNNER ADVANCE DX multifunction devices offer extensive security features to harden your defenses.
You can close unused ports, encrypt hard drives, and set up data flow protocols that can help to minimize your exposure to data breaches. Our expert field engineers can help you protect your document workflows without compromising the productivity and efficiency of your workforce.

Access Control
Controlling access begins by authenticating users at the printer or multifunction device. This can be done with a PIN code, a password, or a proximity card. Users can be assigned privileges by an administrator, authorizing them to have access to certain features and functions on the device (copying, printing, scanning, faxing, etc.).
uniFLOW Online is designed to help save your organization time and money and provide business and security controls over your entire printer and multifunction printer fleet.

Secure your devices from malware and tampering.
The Canon imageRUNNER ADVANCE series is designed with security in mind. These devices can prevent tampering by prohibiting the installation or execution of programs without a digital signature applied by Canon. The following program-tampering detection functions are in place to counter unknown attacks.*
System Verification at Startup
Once enabled, the Verify System at Startup function runs a process during startup to verify that tampering of boot code, OS, firmware, and MEAP applications has not occurred. If tampering of one of these areas is detected, the system will restart using a "Golden Master" that is known good . By using the hardware as the “Root of Trust,” enhanced security against software tampering is provided. Furthermore, standard cryptographic technologies (hash, digital signature) are used for verification.
McAfee Embedded Control
Once enabled, McAfee Embedded Control allows only known programs contained in the dynamic whitelist to be executed on the multifunction printer. Any program that is not on the whitelist is considered unauthorized and will not be permitted to execute. This helps prevent worms, viruses, spyware, and other malware from compromising the device. A log of all prevented executions is available in the Audit Log when Runtime Intrusion Detection is enabled.
*Note: These features are only available on third-generation Canon imageRUNNER ADVANCE models and must be enabled. McAfee Embedded Control requires Unified Firmware Platform (UFP) v3.9.
Big Security for Big Printer Fleets
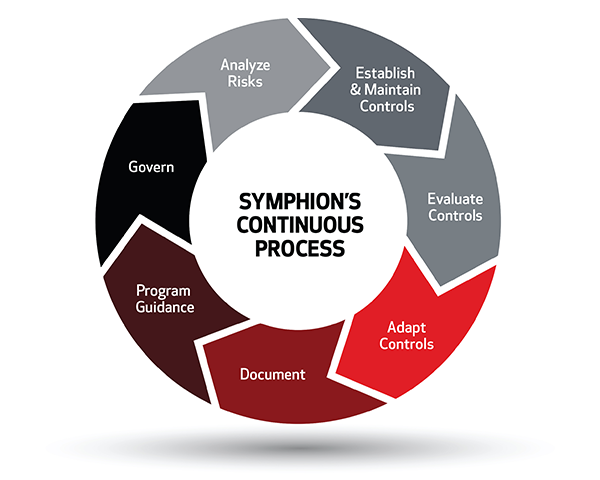
Printer Fleet Cybersecurity as a Service™
Often, many printers on corporate networks are not configured or maintained for cybersecurity. Many cybersecurity plans don’t even mention, let alone address, these elements. Printer fleets can number in the hundreds or thousands with many different makes, models, and ages of devices. Until now, there has been no way to affordably establish and maintain cybersecurity controls in printer fleets. The Answer: Printer Fleet Cybersecurity as a Service.™
Canon Solutions America has a solution designed to help economically and systematically address gaps in device security. It’s the perfect solution for any organization to tune and manage printer security and firmware updates and treat printers like the important computing devices they are. Even more important, we can help keep any brand of printer in your fleet configured and updated for optimal security, all while reducing the work your IT staff has to do with a concierge approach.
Resources

5 Reasons to Consider Zero Trust
Zero Trust is a security framework designed to address the complexities of today’s digital landscape. The core principle of Zero Trust is “never trust, always verify”. This model shifts away from the traditional approach of assuming everything within the network is safe. Instead, Zero Trust assumes that threats can exist both inside and outside the network perimeter.

imageRUNNER ADVANCE Hardening Guide
This guide is intended for anyone who’s concerned with the design, implementation, and securing of office MFDs within a network infrastructure. This might include IT and network specialists, IT security professionals, and service personnel.

imageRUNNER ADVANCE Security
Canon recognizes the importance of information security and the challenges that your organization faces. This white paper provides information security facts for Canon imageRUNNER ADVANCE systems.

imageCLASS/imageRUNNER Security
Canon recognizes the importance of information security and the challenges that your organization faces. This white paper provides information security facts for Canon imageCLASS/imageRUNNER devices sold by Canon Solutions America.

Device Security Overview Brochure
Canon Solutions America has a Five Pillars of Security approach to supporting the protection of information. The pillars are Device Security, Document Security, Information Security, Print Security, and Cybersecurity.

How to Choose a Printer that's Hard to Hack
Office printers and multifunctional devices can be easy targets for cybercriminals. If they’re connected to the internet, they can be hacked from outside your walls, just like computers and servers. Here are several methods to help harden your defenses.

Printers Are Endpoints Too. Are Yours Secure?
Most organizations have deployed endpoint protection solutions for computers. IS THAT ENOUGH?

uniFLOW Device Security Brochure
uniFLOW Online is a cloud-based printing, scanning, and accounting solution that’s easy to configure and secure. The solution extends the standard functionality of imageRUNNER ADVANCE DX, imagePRESS Lite, and compatible imageCLASS X models by adding My Print and Scan Anywhere, mobile printing, and more, to support users whether they're in the office or at home.

Symphion Print Fleet Cybersecurity as a Service
Weaknesses In Your Print Fleet Expose Your Entire Enterprise—What To Do?
Printers on corporate networks are often not configured or maintained with cybersecurity hygiene. Each unprotected printer not only exposes your data, but also your customers’ data and your entire business to unnecessary risk.

Securing Your Print Fleet: What to Do?
No Longer the Forgotten Endpoints: Symphion’s Printer Fleet Cybersecurity as a Service
Printers aren’t going away. They’re the second most prevalent endpoint on most corporate and government networks. Yet, they’re the least visible, least controlled, and least secured.
Many variables can impact the security of a customer’s device and data. Canon does not warrant that the use of services, equipment, or related features detailed herein will eliminate the risk of potential malicious attacks, or misuse of devices or data or other security issues.
